Introduction
Google recently published a new blog post on Kyber. Let's try getting ML-KEM / Kyber working in Google Chrome 131 and Firefox Nightly 133.
OpenSSL 3+ exposes an API for SSL-providers that allows us to only compile the provider instead of having to recompile the application itself.
Disclaimer
liboqs is a research project, while it aims to work and become production-ready, it's primarily there to test new algorithms.
For a production deployment you will likely want BoringSSL or an alternative SSL library.
Dependencies on Fedora 40
sudo dnf -y install astyle gcc python3-pytest openssl-devel
sudo dnf -y install python3-pytest-xdist unzip libxslt graphviz python3-yaml valgrind
sudo dnf -y install doxygen ninja-build cmake
sudo dnf -y install git
Install HAProxy with:
sudo dnf -y install haproxy
I would highly recommend creating a new build user and compiling under that user:
adduser build
passwd build
su - build
gpasswd -a build wheel
The install steps can then be run with sudo or by switching to the root user.
Compiling and installing liboqs
Clone the liboqs repository with:
git clone https://github.com/open-quantum-safe/liboqs
Create a build directory:
mkdir build && cd build
cmake -GNinja ..
ninja -j $(nproc)
Once it's compiled run:
sudo ninja install
Compiling and installing oqs-provider
By the time you are reading this, this pull request
might be merged and the associated issue closed.
If they are, you can just do git clone https://github.com/open-quantum-safe/oqs-provider.git instead.
However at the time of writing the branch that works correctly in browsers is the following:
git clone https://github.com/open-quantum-safe/oqs-provider.git -b bhe-hybridreverse
cd oqs-provider
mkdir build && cd build
cmake -S ..
cmake --build .
The OpenSSL provider will then available in: /home/build/oqs-provider/build/lib/oqsprovider.so
Create a new directory to hold the ssl-providers:
sudo mkdir -p /etc/haproxy/ssl-providers/
cp /home/build/oqs-provider/build/lib/oqsprovider.so /etc/haproxy/ssl-providers/
Configuring HAProxy
Edit /etc/haproxy/haproxy.cfg and add the following lines in the global section of the configuration:
ssl-provider-path /etc/haproxy/ssl-providers/
ssl-provider oqsprovider
Add or modify a SSL-enabled bind line similar to the following:
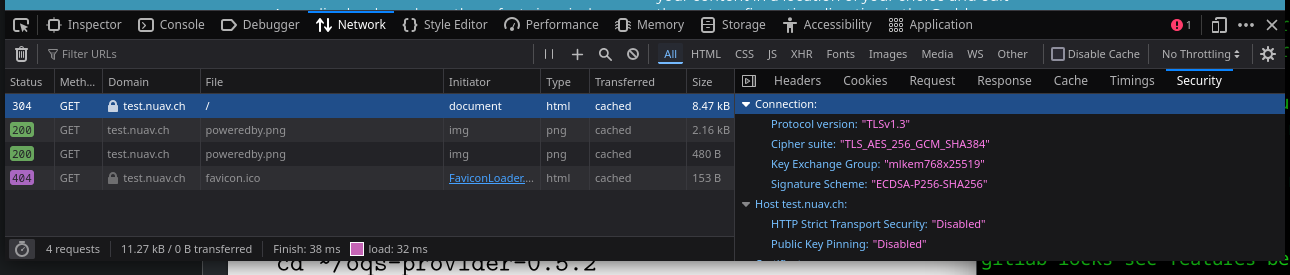
bind *:443 ssl crt /etc/pki/haproxy alpn h2,http/1.1 curves x25519_kyber768:X25519MLKEM768:x25519:secp256r1:secp384r1
X25519MLKEM768 is the new variant of kyber that is going to be supported going forward in Google Chrome 131+.
Run a configuration check with:
haproxy -V -c -f /etc/haproxy/haproxy.cfg
Reload HAProxy with:
systemctl reload haproxy
Screenshots from Google Chrome dev release (131)
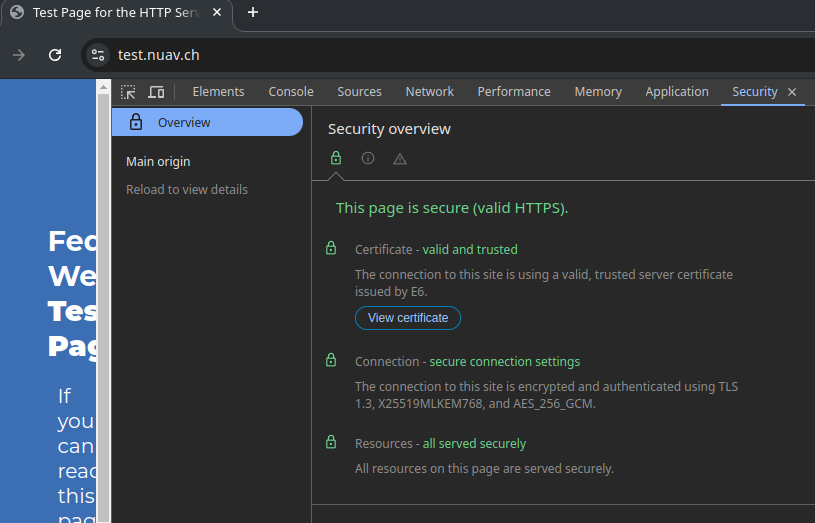
Screenshots from Firefox Nightly (133.0a1)